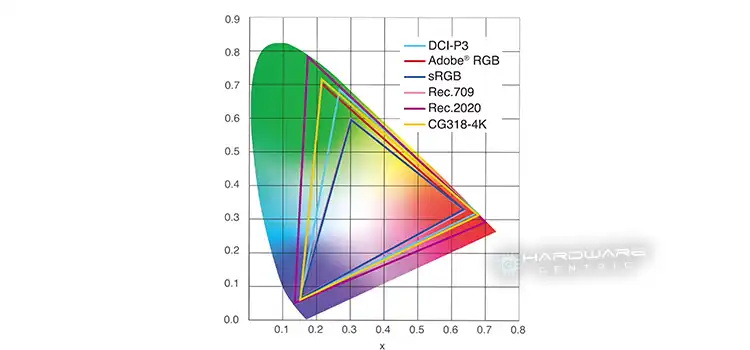
45 NTSC to sRGB Converter for Monitors | Does Such Thing Exist?
Disappointed with the washed-out colors on your 45 NTSC monitor? You’re not alone! Many users mistakenly search for a “45 NTSC to sRGB converter” to achieve the rich, accurate colors they crave. But the truth is, such a converter doesn’t exist. Fear not, though! There are some secrets to getting superb sRGB-like color accuracy on…